Connecting to PSTSec via SSL
Configuring an SSL connection between CTP and PSTSec
In CTP we can point to PSTSec to configure users as described in this topic Integrating CTP with LDAP/AD. In this discussion we indicate that you can configure these settings by navigating to the Security Configuration Menu
From here you can connect to a the PSTSec service by inticating the URL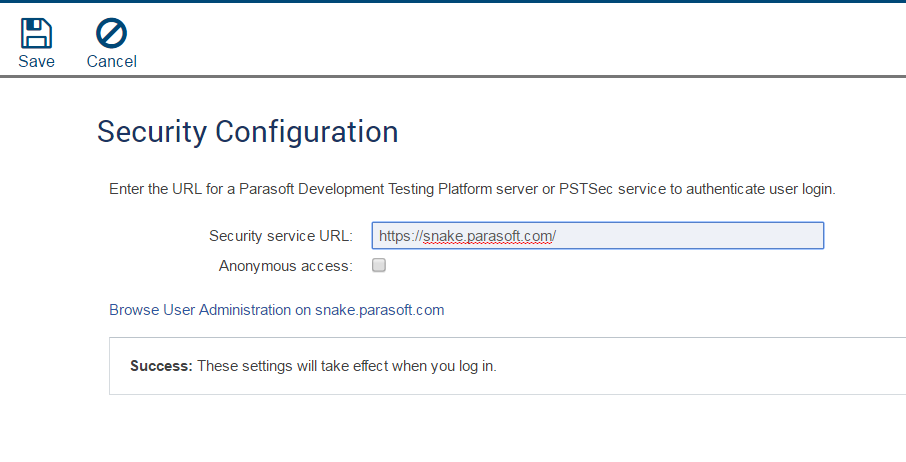
There are 2 location that the PSTSec service can be hosted
- The Development Testing Platform
- As a standalone service (PSTSec.war)
Either way the configuration will be the same but you may want to connect to the service over a secure channel (Https). To do this you will require a few things
Prerequisites
- A certificate/private key pair that CTP will accept. This generally means at minimum a self-signed certificate/private key pair whose common name (CN) parameter matches the fully qualified name of the server. So if the server that is hosting PSTSec's URL is http://myserver.mycompany.com, the CN parameter should be "myserver.mycompany.com". Depending on your company's security policy, you may also need the certificate signed by your company's certificate authority.
- Access to the DTP or CTP installation directories depending on whether you are using the standalone PSTSec or the one supplied with DTP.
Configuring PSTSec to send a certificate
If you need to generate a self-signed certificate you can use the following command from your Java installation
<JAVA_HOME>\bin keytool -genkey -keyalg RSA -alias dtp -keystore "D:\Program Files\Parasoft\DTP\tomcat\conf\newkeystore" -storepass changeit -validity 360 -keysize 2048
Follow the onscreen prompts
Notice how I am supplying the machine fully qualified machine name that will be hosting PSTSec in the CN area?
From here you will get a new keystore. You then need to supply this to PSTsec so that it serves it up to any application that calls it. To do this we need to do the following
Navigate to the server.xml file for pstsec
For DTP this will be
<DTP Installation directory>\tomcat\conf\server.xmlFor Standalone PSTSec this will be
<TOMCAT installation directory>\conf\server.xmlSearch for the text SSLEnabled="true"
You will see a section that looks like this:<Connector SSLEnabled="true" URIEncoding="UTF-8" clientAuth="false" connectionTimeout="20000" enableLookups="false" keyAlias="mykey" keystoreFile="../lib/cacerts" keystorePass="changeit" keystoreType="JKS" maxThreads="150" port="9443" protocol="HTTP/1.1" scheme="https" secure="true" server="Parasoft Server" sslProtocol="TLS" truststoreFile="../lib/cacerts" truststorePass="changeit" truststoreType="JKS"/>
In this section:Modify keystoreType to one of PKCS12, JKS, BKS, UBER, or PEM depending on the type of keystore you're using
- Modify keystoreFile to point to your keystore file. Use forward slashes (/) instead of backward slashes (), Ex: C:/Users/myUser/keystore.jks
- Save and restart
At this point PSTsec will serve up a certificate to CTP whenever it is called via SSL. To check this navigate to the URL in a browser (Example https:\\HOST:PORT\pstsec). You should get a security exception if you have not added an exception. You can use this to your advantage
Configuring CTP to Trust the new Certificate
If you have a browser open to the new PSTSec url you can actually grab the certificate. Usually in the upper corner of the browser (On a secure connection) you will see a Lock
If you click on this you can view details
Depending on your browser, choices will be different from here but the path is essentially the same. You want to look at the details
Export the certificate
This is the same certificate you added to PSTSec but instead of being the full keystore it is just the Certificate. You can now simply import this certificate into CTP's trust store. The easiest way to do this is to use keytool
%JAVA_HOME%\bin\keytool -import -trustcacerts -keystore %JAVA_HOME%\jre\lib\security\cacerts -storepass changeit -alias pstsec -file <PATH TO YOUR CERTIFICATE>
Note: For my example I am importing into %JAVA_HOME% because that is the Java my CTP is using. If your CTP is using a different java, import the cert into its cacerts
- Go ahead and restart CTP.
At this point you should be able to connect over SSL.